Describe the Specific Vulnerability Metrics Used by Each Catalog
People lack adequate occupation. It measures how the vulnerability is exploited for instance locally or remotely.

Unified Dashboard Preview For Enhanced Security Visualization Qualys Security Blog
Each of the SVI metrics was categorized into national and state-specific tertiles low moderate and high social vulnerability based on their national among all US.
. Cal Polys IT Security Standard. The CVSS Score chart displays how many of your vulnerabilities fall into each of the CVSS score ranges. The Base metric group represents the intrinsic characteristics of a vulnerability that are constant over time and across user environments.
The Common Vulnerability Scoring System CVSS is an open framework for communicating the characteristics and severity of software vulnerabilities. This score is based on access complexity required authentication and impact on data. You can however use a relational database and track software instances on specific servers or networking devices.
Common Vulnerability Scoring System CVSS A universal way to convey vulnerability severity and help determine urgency and priority of responses A set of metrics and formulas Solves problem of multiple incompatible scoring systems in use today Under the custodial care of FIRST CVSS-SIG Open usable and understandable by anyone. More information is available in the CVSS documentation. Vulnerability scanning can be used at a broader level to ensure that campus information security practices are working correctly and are effective.
The mission of the CVE Program is to identify define and catalog publicly disclosed cybersecurity vulnerabilities. D It can index enrich and aggregate log data from applications. None 00 partial 0275 complete 066 The metrics values are combined with formulas that give different weights to the base metrics Base subscores for impact and exploitability.
Pouring through spreadsheets and creating oversized PDFs is no longer enough to ensure that critical vulnerabilities will be remediated in time. Counties or state. In some cases based off of these factors a vulnerability that has a CVSS score below 10 might pose more of a risk to the organization than a.
The score ranges from 1 to 10 with 10 being the worst so you should prioritize the vulnerabilities with the higher numbers. Specific measurable attainable repeatable and time-dependent. FAQs has moved to the new Frequently Asked Questions FAQs page on the CVEORG website.
The Base metrics produce a score ranging from 0 to 10 which can then be modified by scoring the Temporal and Environmental. The CVSS score is calculated based on several metrics including exploitability attack complexity impact and level of authentication needed to exploit the vulnerability. For vulnerability notes that cover more than one vulnerability eg multiple CVE IDs the CVSS metrics will apply to the vulnerability with the highest CVSS base metric.
In the Executive Vulnerability Metrics dashboard there are 4 matrices that correlate vulnerabilities from the date the vulnerability is published to the time the vulnerability is identified by SecurityCenter - the time a patch is available and the time the risk is mitigated. By providing specific details about the ease of exploit the privilege gained and the age of the vulnerability security analysts have a simple objective answer to provide to system administrators. Alexander goes on to distinguish six vulnerability types p.
Security teams must apply organization-specific metrics to vulnerability management to. To use CVSS effectively it is important to calculate your own current and specific Temporal and Environmental metrics. Security teams today are constantly overwhelmed with the sheer quantity of potential vulnerabilities that they must mitigate.
Tuned to fit a specific organization or situation. Computing Devices includes requirements addressing scanning computing devices for vulnerabilities and remediating any found vulnerabilities in a timely manner. The phased quarterly transition process began on September 29 2021 and will last for up to one year.
CVE is a program launched in 1999 by MITRE a nonprofit that operates research and development centers sponsored by the federal government. CVSS v30 Metric Groups. A It can analyze critical diagnostic information that describes how resources are performing and being accessed.
The edgescan report has become a reliable source for truly representing the global state of cyber security. These matrices provide you with numbers that executives need to understand and properly. This definition identifies vulnerability as a characteristic of the element of interest community system or asset which is independent of its exposure.
To be truly useful metrics should also indicate the degree to which security goals are being met and drive actions taken to improve an organizations overall security program. There are six base metrics that capture the most fundamental features of a vulnerability. This report aims to demonstrate the state of full stack security based on edgescan data for 2018.
Security analysts not only review metrics currently in place but also need to ensure they are aligned with the specific organizational and business goals. CVSS is composed of three metric groups Base Temporal and Environmental each consisting of a set of metrics as shown in Figure 1. County-level social vulnerability rankings for 15 SVI indicators four SVI themes and the overall SVI 20 total SVI metrics were used.
Each metric has a number assigned to each possible value AccessComplexity. C It enables you to analyze cloud resources using custom metrics. Base Temporal and Environmental.
The risk level for each vulnerability Critical High Medium is governed by a specific score CVSS Score. CVSS consists of three metric groups. In other words good metrics must be meaningful to specific organizational goals and key performance indicators.
High 035 medium 061 low 071 Integrity. This attribute is useful for network devices and servers but rarely applies to software. However in common use the word is often used more broadly to include the elements exposure.
B It is a centralized single pane of glass for all logs in a tenancy. Edgescan Vulnerability Stats Report. Its purpose is to identify and catalog vulnerabilities.
1 Access Vector AV. This year we took a deeper look at vulnerability metrics from a known. The CVE Program has begun transitioning to the all-new CVE website at its new CVEORG web address.
Vulnerability varies significantly within a community and over time. The more remote an attacker can be to attack an information asset the greater the vulnerability score. As it is mainly the result of social economic political and cultural factors in decision making vulnerability is constructed socially 2013 p.
Effective metrics are often referred to as SMART ie. Describe the use of an IP address when deciding which attributes to track for each information asset.

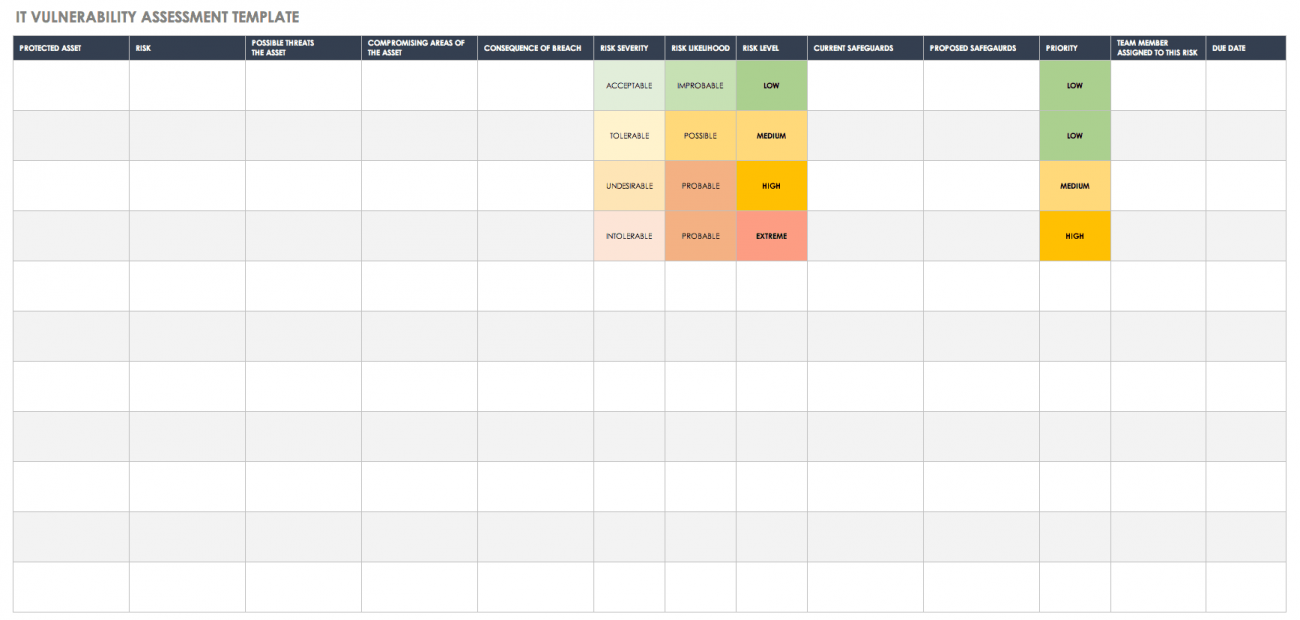
Free Vulnerability Assessment Templates Smartsheet

Cybersecurity Scorecard With Kpis For Data Security Strategy Map Data Security Cyber Security
No comments for "Describe the Specific Vulnerability Metrics Used by Each Catalog"
Post a Comment